Cracking A Vigenere Encryption
NATURA AMORE ARTE ANIMALI CITT NATALIZI RICORRENZE PAESAGGI FIORI VARIE Dipinto di Salvador Domnec Felip Jacint Dal, Olio su Tela Noia alla finestra. History of Cryptography. PLEASE NOTEThis is not intended to be a scholarly work nor. The fact and fiction of this discipline is endless. Our. intention in presenting this material is to provide interested persons. We welcome suggestions, corrections, additions. You can download a PDF version of this document here. Throughout history, cryptography has had dramatic effects on the outcome of wars, monarchies and the lives of individuals. One example of this is the successful. Cryptografie of geheimschrift uit het Grieks, kryptei verborgen, en grfo schrijven houdt zich bezig met technieken voor het. Cisco Cracking and Decrypting Cisco Type 5 Passwords, Type 7 Passwords. Cracking A Vigenere Encryption' title='Cracking A Vigenere Encryption' />

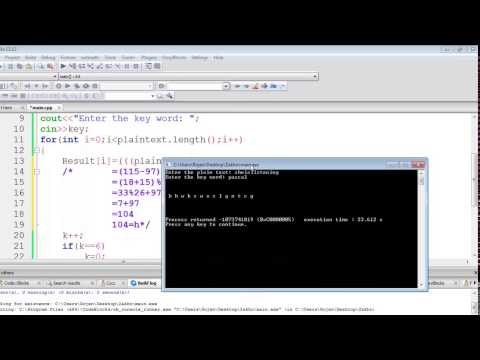 Why not head over to the Cypher Research Laboratories. IN THE BEGINNINGIt is believed that the oldest known text to contain. Egyptian town of MENET. Get cracking Caesar Shifts. The. The Vigenere encryption was the creation of the French diplomat, Blaise de Vigenere in the 1500s. It combines multiple different. Kryptos is a sculpture by the American artist Jim Sanborn located on the grounds of the Central Intelligence Agency CIA in Langley, Virginia. Since its dedication. Cypher Research Labs CRL is an Australian owned company specialising in the design and manufacture of high grade encryption, associated products, covert. KHUFU where the hieroglyphic inscriptions on the tomb of the nobleman. KHNUMHOTEP II were written with a number of unusual symbols to confuse. In 5. BC the SPARTANS, a warrior society famed for. This device. a cylinder called a SCYTALE, was in the possession of both the sender. To prepare the message, a narrow. SCYTALE and the message was written across it. Once unwound, for transport to the receiver, the tape displayed only. SCYTALE. of exactly the same diameter. The code, produced by unwinding the. TRANSPOSITION cypher, that is, one where the letters remain. This is still the basis for many. The other major ingredient of these modern techniques. ADDITIVESUBSTITUTION cypher. Although the Greek writer POLYIBUS. JULIUS CAESAR. Messages were encoded by substituting the letter in. A became D. V became Y etc. The reason why a substitution of three letters, and. In an essay written in 1. Italian LEON BATTISTA. ALBERTI who is often called the father of western cryptography. POLY ALPHABETIC cyphers. Although he had made the most important. It was left for others, the best known being. French cryptographer BLAISE DE VIGENERE to devise a practical. VIGENERE SQUARE. At the time, and for a considerable time afterwards this technique. Le Chiffre Indechiffrable. There. was however a weakness in this cypher waiting to be exploited because. Probably in 1. 85. CHARLES BABBAGE, developed the. Vigenere square. Unfortunately, due to his. Britain could decrypt Vigenere. Crimea, this fact was not discovered until the. The honour of developing the statistical attack. Vigenere was to go to the Prussian KASISKI. KASISKI TEST. WWI, THE WAR TO END ALL WARSTHE. ZIMMERMANN TELEGRAMOn the first day of hostilities, the British cable. TELCONIA located and cut Germanys transatlantic cables. Brennenstuhl Pm 230 Manual. Sweden or. American owned cables. Both means ran through the UK and soon all. German traffic was routinely routed to ROOM 4. Royal Navys. cypher organisation. On or about January 1. Room 4. 0 cryptanalyst. WILLIAM MONTGOMERY and NIGEL DE GRAY, were given a message encrypted. German Foreign Office code, a BOOK CYPHER number 0. By the. next morning they had deduced enough of the message to be chilled. Sent by the German Foreign Minister ZIMMERMANN to. Mexican President via the German Embassies in Washington and Mexico. City, it advised the President of Mexico that Germany proposed to. February and that he should. German help, attack the US and also convince the Japanese to. In short order the full text was recovered and presented. US President WILSON. On April 2, 1. 91. US declared war on Germany and by 1. Germany had been defeated. To obscure the source of the original intercept. Mexico, Room 4. 0, using a British. Mexico, obtained a copy of the edited USMEXICO version of. Doom Rpg Game For Pc'>Doom Rpg Game For Pc. Zimmermann cable. This of course differed from the original. Washington. to Mexico City. The decrypt of this was the copy released to the US. British had obtained their. Mexico but decryption of the original. London. The Germans spotted the difference and took the. The deception was complete and the source was safe. The code breakers. Winston Churchill or. Towards the end of WWI the head of cryptographic. US Army MAJOR JOSEPH MAUBORGNE introduced the concept. RANDOM keys. This would take the form of. Using the Vigenere technique, each page is to be used to encrypt and. ONE message and then destroyed. The weakness of the Vigenere. This new technique injected. Attacks seeking to exploit these weaknesses such as the Babbage. Kasiski tests, would fail. A key length of as little as 2. KEY EXHAUSTION attack, the cryptographic equivalent of Custers. This method is still in use today, called the ONE. TIME LETTER PAD or OTLP, and is used for encrypting the most secret. OTLP is still the only admitted system. THE NOT QUITE SO DISTANT PASTThere can be no doubt that times of conflict focus. This in turn leads. The first world. war showed the importance of cryptography on the battlefield, and. The second world war. Struggling under the weight of axis forces in the. Japan in the east, the use of encryption by the allied nations. In the evening of 1. Japanese 8th fleet sent messages concerning the itinerary. CIC of the Japanese Fleet. To protect this vital information, the message was encrypted using. Japanese Naval code 2. JN 2. 5. This message, like many others, was. US intercept station in Hawaii and the Royal Australian. Airforce 1 Wireless Unit in Townsville, North Queensland. Unknown. to the Japanese or, as some suggest, suspected but ignored, the Americans. US. army and navy code used in the Spanish American war of 1. The. allies ability to intercept and decrypt this message led directly. ADMIRAL YAMAMOTO, over Bougainville. United States P 3. Lightning piloted. CAPT THOMAS G. LAMPHIER. This resulted in the death of the most. Japanese navy robbing. As an adjunct to this, on the occasion of the 5. Australian Defence Signals Directorate DSD. United States of America, the United Kingdom. New Zealand and Canada made presentations. Underscoring under the. US National Security. Agency NSA presented DSD with. Japanese. PURPLE cypher machine. For those with a penchant for conspiracy theories. JN 2. 5 and associated radio traffic. Betrayal at Pearl Harbor makes interesting reading. In this book the authors one a respected WWII cryptographer CAPT. ERIC NAVE argue that the British government intercepted all of the. Japanese radio traffic which identified. Pearl Harbour attack. They also suggest that the British. Americans in the hope that this would drag them. Michael Smith, author of Station. X and The Emperors Codes suggests that based on. Naves unpublished autobiography held at the Australian War Memorial. The Emperors. Codes 2. More widely known and reported today is the importance. ULTRA, the British codeword for SIGINT derived. Axis radio messages and, in particular, from. German ENIGMA. traffic. The ENIGMA machine was developed by a German ARTHUR. SCHERBIUS and was patented in 1. Despite a lack of commercial success. German. Navy in 1. Army in 1. 92. 8 and the Air Force in 1. It was also. introduced into service with other sections of the German government. Such an extensive use of Enigma being due almost entirely to revelations. British decryption of German wartime messages made by Winston. Churchill in his book World Crisis published in 1. This. cryptographic door opened by Churchill was taken of its hinges in. British Royal Navy. Room 4. 0. Scherbiuss Enigma could not have. The secrecy that surrounds western codes. The watchword today is never. The jibe often directed at the. NSA suggesting that their initials stand for never say anything. Unfortunately for the WWI allies their decryption. German cypher traffic had ceased by early 1. Enigma. The Enigma is referred to as an OFF LINE cypher system. Enigma was a manual system whereby each. KEYBOARD TASTATUR and the. LAMP BOARD. GLUHLAMPENFELD. This letter was transcribed on a message. This. cyphertext message was then transmitted by radio using Morse code. Decryption followed the same procedure with the cyphertext letter. ChallengesCryptanalysis Hash SHA 2 Root Me Hacking and Information Security learning platformDefte. November 2. 01. 7 at 1. Godamn, people like you piss me off.
Why not head over to the Cypher Research Laboratories. IN THE BEGINNINGIt is believed that the oldest known text to contain. Egyptian town of MENET. Get cracking Caesar Shifts. The. The Vigenere encryption was the creation of the French diplomat, Blaise de Vigenere in the 1500s. It combines multiple different. Kryptos is a sculpture by the American artist Jim Sanborn located on the grounds of the Central Intelligence Agency CIA in Langley, Virginia. Since its dedication. Cypher Research Labs CRL is an Australian owned company specialising in the design and manufacture of high grade encryption, associated products, covert. KHUFU where the hieroglyphic inscriptions on the tomb of the nobleman. KHNUMHOTEP II were written with a number of unusual symbols to confuse. In 5. BC the SPARTANS, a warrior society famed for. This device. a cylinder called a SCYTALE, was in the possession of both the sender. To prepare the message, a narrow. SCYTALE and the message was written across it. Once unwound, for transport to the receiver, the tape displayed only. SCYTALE. of exactly the same diameter. The code, produced by unwinding the. TRANSPOSITION cypher, that is, one where the letters remain. This is still the basis for many. The other major ingredient of these modern techniques. ADDITIVESUBSTITUTION cypher. Although the Greek writer POLYIBUS. JULIUS CAESAR. Messages were encoded by substituting the letter in. A became D. V became Y etc. The reason why a substitution of three letters, and. In an essay written in 1. Italian LEON BATTISTA. ALBERTI who is often called the father of western cryptography. POLY ALPHABETIC cyphers. Although he had made the most important. It was left for others, the best known being. French cryptographer BLAISE DE VIGENERE to devise a practical. VIGENERE SQUARE. At the time, and for a considerable time afterwards this technique. Le Chiffre Indechiffrable. There. was however a weakness in this cypher waiting to be exploited because. Probably in 1. 85. CHARLES BABBAGE, developed the. Vigenere square. Unfortunately, due to his. Britain could decrypt Vigenere. Crimea, this fact was not discovered until the. The honour of developing the statistical attack. Vigenere was to go to the Prussian KASISKI. KASISKI TEST. WWI, THE WAR TO END ALL WARSTHE. ZIMMERMANN TELEGRAMOn the first day of hostilities, the British cable. TELCONIA located and cut Germanys transatlantic cables. Brennenstuhl Pm 230 Manual. Sweden or. American owned cables. Both means ran through the UK and soon all. German traffic was routinely routed to ROOM 4. Royal Navys. cypher organisation. On or about January 1. Room 4. 0 cryptanalyst. WILLIAM MONTGOMERY and NIGEL DE GRAY, were given a message encrypted. German Foreign Office code, a BOOK CYPHER number 0. By the. next morning they had deduced enough of the message to be chilled. Sent by the German Foreign Minister ZIMMERMANN to. Mexican President via the German Embassies in Washington and Mexico. City, it advised the President of Mexico that Germany proposed to. February and that he should. German help, attack the US and also convince the Japanese to. In short order the full text was recovered and presented. US President WILSON. On April 2, 1. 91. US declared war on Germany and by 1. Germany had been defeated. To obscure the source of the original intercept. Mexico, Room 4. 0, using a British. Mexico, obtained a copy of the edited USMEXICO version of. Doom Rpg Game For Pc'>Doom Rpg Game For Pc. Zimmermann cable. This of course differed from the original. Washington. to Mexico City. The decrypt of this was the copy released to the US. British had obtained their. Mexico but decryption of the original. London. The Germans spotted the difference and took the. The deception was complete and the source was safe. The code breakers. Winston Churchill or. Towards the end of WWI the head of cryptographic. US Army MAJOR JOSEPH MAUBORGNE introduced the concept. RANDOM keys. This would take the form of. Using the Vigenere technique, each page is to be used to encrypt and. ONE message and then destroyed. The weakness of the Vigenere. This new technique injected. Attacks seeking to exploit these weaknesses such as the Babbage. Kasiski tests, would fail. A key length of as little as 2. KEY EXHAUSTION attack, the cryptographic equivalent of Custers. This method is still in use today, called the ONE. TIME LETTER PAD or OTLP, and is used for encrypting the most secret. OTLP is still the only admitted system. THE NOT QUITE SO DISTANT PASTThere can be no doubt that times of conflict focus. This in turn leads. The first world. war showed the importance of cryptography on the battlefield, and. The second world war. Struggling under the weight of axis forces in the. Japan in the east, the use of encryption by the allied nations. In the evening of 1. Japanese 8th fleet sent messages concerning the itinerary. CIC of the Japanese Fleet. To protect this vital information, the message was encrypted using. Japanese Naval code 2. JN 2. 5. This message, like many others, was. US intercept station in Hawaii and the Royal Australian. Airforce 1 Wireless Unit in Townsville, North Queensland. Unknown. to the Japanese or, as some suggest, suspected but ignored, the Americans. US. army and navy code used in the Spanish American war of 1. The. allies ability to intercept and decrypt this message led directly. ADMIRAL YAMAMOTO, over Bougainville. United States P 3. Lightning piloted. CAPT THOMAS G. LAMPHIER. This resulted in the death of the most. Japanese navy robbing. As an adjunct to this, on the occasion of the 5. Australian Defence Signals Directorate DSD. United States of America, the United Kingdom. New Zealand and Canada made presentations. Underscoring under the. US National Security. Agency NSA presented DSD with. Japanese. PURPLE cypher machine. For those with a penchant for conspiracy theories. JN 2. 5 and associated radio traffic. Betrayal at Pearl Harbor makes interesting reading. In this book the authors one a respected WWII cryptographer CAPT. ERIC NAVE argue that the British government intercepted all of the. Japanese radio traffic which identified. Pearl Harbour attack. They also suggest that the British. Americans in the hope that this would drag them. Michael Smith, author of Station. X and The Emperors Codes suggests that based on. Naves unpublished autobiography held at the Australian War Memorial. The Emperors. Codes 2. More widely known and reported today is the importance. ULTRA, the British codeword for SIGINT derived. Axis radio messages and, in particular, from. German ENIGMA. traffic. The ENIGMA machine was developed by a German ARTHUR. SCHERBIUS and was patented in 1. Despite a lack of commercial success. German. Navy in 1. Army in 1. 92. 8 and the Air Force in 1. It was also. introduced into service with other sections of the German government. Such an extensive use of Enigma being due almost entirely to revelations. British decryption of German wartime messages made by Winston. Churchill in his book World Crisis published in 1. This. cryptographic door opened by Churchill was taken of its hinges in. British Royal Navy. Room 4. 0. Scherbiuss Enigma could not have. The secrecy that surrounds western codes. The watchword today is never. The jibe often directed at the. NSA suggesting that their initials stand for never say anything. Unfortunately for the WWI allies their decryption. German cypher traffic had ceased by early 1. Enigma. The Enigma is referred to as an OFF LINE cypher system. Enigma was a manual system whereby each. KEYBOARD TASTATUR and the. LAMP BOARD. GLUHLAMPENFELD. This letter was transcribed on a message. This. cyphertext message was then transmitted by radio using Morse code. Decryption followed the same procedure with the cyphertext letter. ChallengesCryptanalysis Hash SHA 2 Root Me Hacking and Information Security learning platformDefte. November 2. 01. 7 at 1. Godamn, people like you piss me off.